Optimize for Efficiency
Streamline your IT Infrastructure, Cybersecurity, and Cloud Operations.
Connect NowUnlock enhanced application performance, security, and usability to deliver greater value.
Cost Optimization
Resource Right-Sizing : Periodic analysis and adjustment of cloud resources to align usage with actual demand, utilizing auto-scaling, reserved and spot instances, and eliminating idle resources to ensure efficient and cost-effective cloud spend.
Lifecycle Management : Comprehensive administration of cloud resources from deployment to retirement, including planning, provisioning, monitoring, optimizing, and eventually decommissioning cloud assets to ensure efficiency, security, and cost-effectiveness throughout their lifecycle.
Operational Efficiency
Automation and Orchestration : Implement Infrastructure as Code (IaC) and configuration management tools to automate the provisioning, configuration, and management of cloud resources, ensuring consistent, repeatable, and scalable deployments while reducing manual errors and enhancing operational efficiency.
Monitoring and Logging : Establish comprehensive monitoring and logging solutions to track performance metrics, detect anomalies, and enable prompt identification and resolution of issues.
Security Optimization
Identity and Access Management (IAM) : Prevent unauthorized access by applying and enforcing least privilege principles and multi-factor authentication.
Data Encryption : Protect sensitive information and ensure its confidentiality, whether at rest or in transit, by applying industry-standard protocols and key management practices.
Performance Optimization
Load Balancing and Autoscaling : Configure load balancers and implement autoscaling policies to dynamically adjust resource allocation based on demand patterns, enhancing reliability, optimizing performance and application responsiveness.
Database Optimization : Implement indexing, query refinement, and schema design to ensure rapid, efficient, and scalable data retrieval.
Vulnerability Management
Perform regular vulnerability assessments and penetration testing to detect and remediate security vulnerabilities in IT systems and applications.
Establish patch management processes to ensure the timely application of security patches and updates throughout the infrastructure.
Continuous Improvement
Adopt a cybersecurity posture of continuous improvement by conducting regular reviews, updating threat intelligence, and proactively adjusting security controls and policies in response to emerging threats and vulnerabilities.
Continuously track various infrastructure metrics to ensure optimal performance, detect bottlenecks, and implement necessary adjustments to improve efficiency and enhance the user experience.
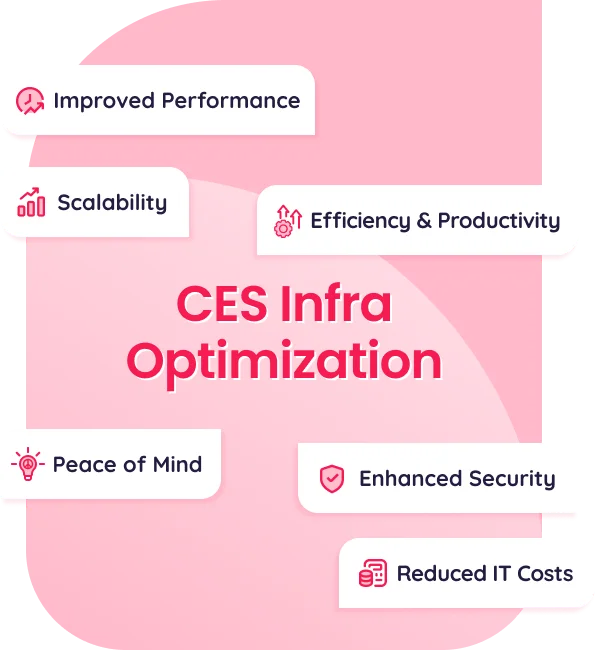
Why Choose CES Infra for Your Optimization Needs?
Minimize downtime and ensure optimal performance of your IT infrastructure through proactive maintenance and expert monitoring.
Our robust security solutions and data protection strategies safeguard your critical information from unauthorized access and cyber threats.
By leveraging our expertise, you can free up your internal IT resources to focus on strategic initiatives, leading to cost savings.
Our proactive approach to IT infrastructure management ensures seamless operation and minimizes disruptions, allowing your employees to focus on their core tasks.
We design and implement scalable IT solutions that can adapt to your evolving business demands, ensuring your infrastructure can keep pace with your growth.
With CES Infra managing your IT infrastructure, you can rest assured that your critical systems are in expert hands, allowing you to focus on driving business success.
Efficiency That Drives Results
Maximize performance and cut costs with CES Infra’s optimization strategies. We fine-tune IT resources, implement advanced monitoring, and tighten security for peak efficiency.